
- Details
- Written by: RAINFIRE
- Hits: 4379
PCIe 4.0 NVMe BARROW Waterblock on Sabrent Rocket + 21C Temp Drop w/Heat/Speed Tests & 3950X, 5700XT. Barrow HDM2280-PA Waterblock for NVMe 2280/22110 Size M2, Double Sided Auxiliary Cooling. It wasn't easy to put in between the CPU & GPU Waterblocks. It was difficult to drain and not get anything wet when removing the tubes. Was it worth it? YES! Will I do it again? NO! :) It depends on load as to how much the temperature difference is, but it is at least 21C degrees cooler on average.
- Details
- Written by: RAINFIRE
- Hits: 4867
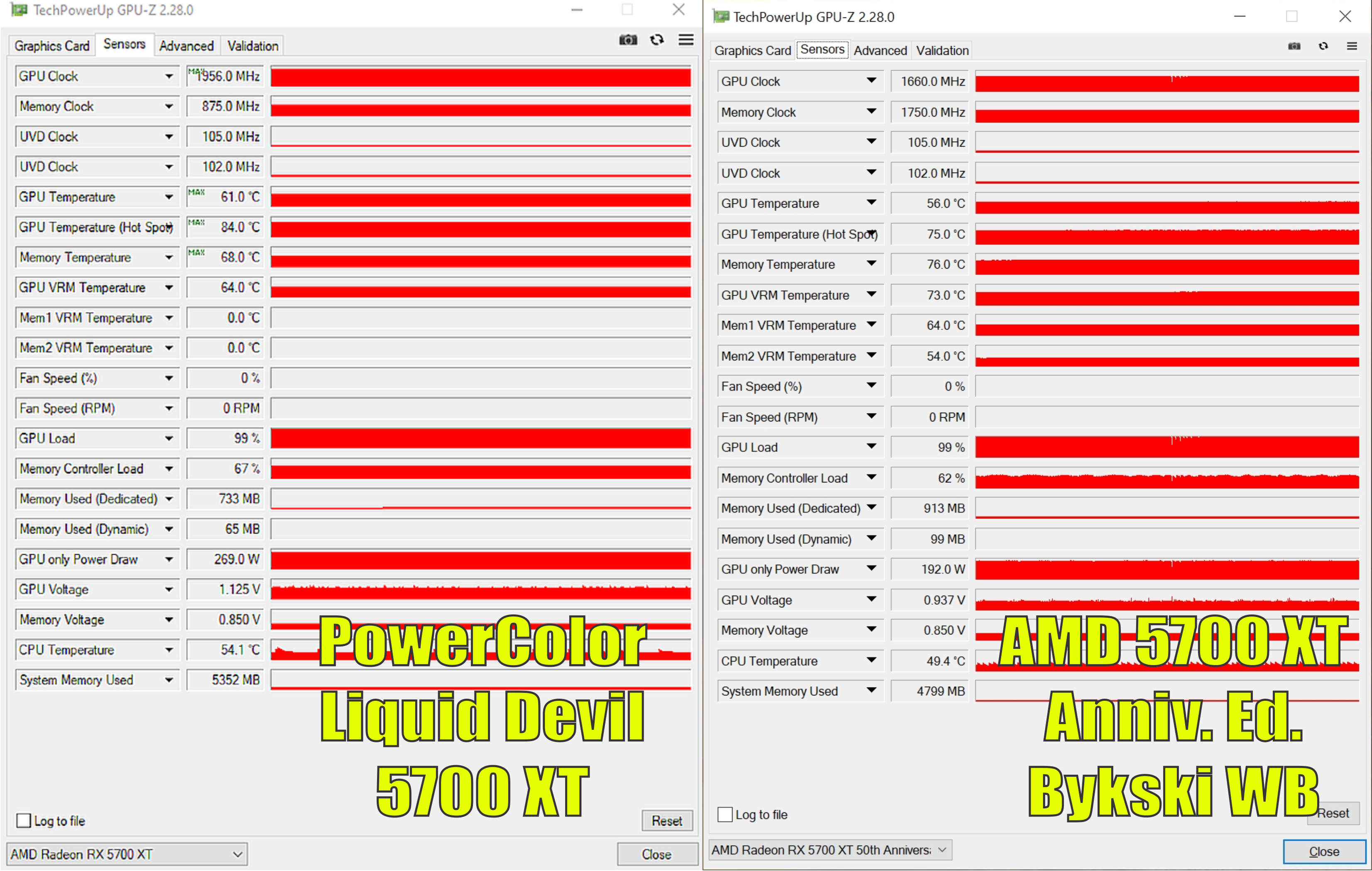
UPDATE: I added a RADEON VII with EK Waterblock to the Comparison. A Discord User and myself tested our Radeon RX 5700 XT's today. We both ran a 15 minute Furmark test. PowerColor Liquid Devil 5700 XT vs AMD 5700 XT Anniv. Ed. with Bykski Water Block. Both had 2 X 360 Radiators and both ended up with inline water at 36C. He used Liquid Devil's UNLEASHED BIOS stock and I used AMD Anniv. Factory OC BIOS stock. He saved time not having to put on WB and I saved $50 and lost an hour. We called it a draw. Above are the results. ALL TESTS WERE RAN ON DEC. 21, 2019.
- Details
- Written by: RAINFIRE
- Hits: 2544
Why Pay More? This G1/4" fitting size and 14mm tubing and connectors is the most common size of watercooling for computers. The ones we look at here are pretty much standard from different vendors and the PRICES ARE MUCH LOWER. There are all sorts of name brands and sizes. Vendors and Big Youtubers try to lock you in to using their custom systems. That's fine if you want to spend $500-$1,000 for watercooling parts (I can think of one huge youtuber specifically). I DON'T WANT TO PAY A $1,000! So check out these, lowest cost, great performing, most standardized size, watercooling parts. If you want to pay more, go watch those big name youtubers and their big name sponsors. All the parts I show are available for low prices below from multiple vendors.
Read more: LOW COST PC Watercooling G1/4" 14mm Parts Explained - Best Deal & Standardized
- Details
- Written by: RAINFIRE
- Hits: 2683
Bykski AMD RX 5700XT WaterBlock, Anniversery Edition & LCD PRE-Installation Video
Also, featuring the Bykski Watercooling Inline Temperature LCD. As soon as the AMD 3950X comes out, I'll try to make another video of the installation and water cooled temperatures.
Read more: Bykski WaterBlock AMD RX 5700XT Anniversary Edition & LCD PRE-Installation Video

![[ Celebrate 40 years of GNU! ]](https://www.gnu.org/gnu40/GNU40_badge-sm.png)
